Provide proof of compliance. The on-site security assessment will include a visual inspection of the entire facility internally and externally.

Physical Security Assessment Template Beautiful Fice Safety Audit Checklist Te Security Assessment Classroom Newsletter Template Preschool Newsletter Templates
Organized into three main categorizes.

. The cornerstone of a good security plan is a current site-specific risk assessment. Physical Security Systems Assessment Guide. All SY0-601 Questions A security assessment determines DES and 3DES are still.
Transit agencies shall complete system-wide Security Risk Assessments to determine the threats. Examples of Specific Assessments in a sentence. Terms in this set 41 Nonverbal communication includes.
Second element to threats. Site specific risk assessment means a technical scientific assessment of the nature and magnitude of the human health or environmental risk as outlined in the Guideline. Understand Site-Specific Risk Assessments and Application.
Get a customized report with your cybersecurity strengths weaknesses and risks. Examines the threat after. Sogns letters signals gestures documents email and various other mediums.
An evaluation of the security provided. See how you compare to other organizations in your industry. Audit of insecure protocols and deprecated encryption.
An impact assessment also known as impact analysis or consequence assessment estimates the degree of overall harm or loss that could occur as a result of the. Attributes of good communication include. It forms the logical basis for physical and personnel security measures employed to achieve graded.
Site Specific Assessments titled Central Interceptor Main Project Works Assessment of Effects on the Environment prepared. This guide will help you determine the likelihood and. This assessment gathers historical and other readily available.
3 intentional or malicious threats. Ad Take the NIST-based Cybersecurity Maturity Assessment from eSentire VMware Carbon Black. Assessment-specific needs and assessors may have to design new methods to collect information not specifically.
Get a customized report with your cybersecurity strengths weaknesses and risks. The Security Threat and Risk Assessment. A security risk assessment identifies assesses and implements key security controls in applications.
Understand ThreatsHazards Vulnerabilities and. Receive a Gap Analysis Risk Remediation Recommendations. To people who work in the security or protection industry threat assessment is the first step in a risk and vulnerability analysis.
Get a complimentary assessment. ExtraHop is your solution. Each facility survey will consist of a walk through and inspection of all areas of the building totaling 86 different.
Ultimately the purpose of a site-specific hazard assessment is to identify hazards determine a path for hazard mitigation increase public safety and reduce the threat of future property. Site security assessment guide An in-depth risk assessment and analysis are the first steps in effective site security planning. Ad Take the NIST-based Cybersecurity Maturity Assessment from eSentire VMware Carbon Black.
21 Systemwide and site-specific Security Risk Assessments. Ad Secure your attack surface against advanced cyber threats. The site-specific assessment process ensures the arrangements between parties for the conduct of research in health service organisations are in place.
A physical security assessment of each building that is used by employees. Ad Assess Current Controls. Ultimately the purpose of a site-specific hazard assessment is to identify hazards determine a path for hazard mitigation increase public safety and reduce the threat of future property.

Determining Risk Impact Risk Assessment Matrix Risk Matrix Risk Analysis Assessment

Risk Assessment Vs Vulnerability Assessment How To Use Both Bmc Software Blogs

Risk Assessment Vs Vulnerability Assessment How To Use Both Bmc Software Blogs

How To Perform It Security Risk Assessment
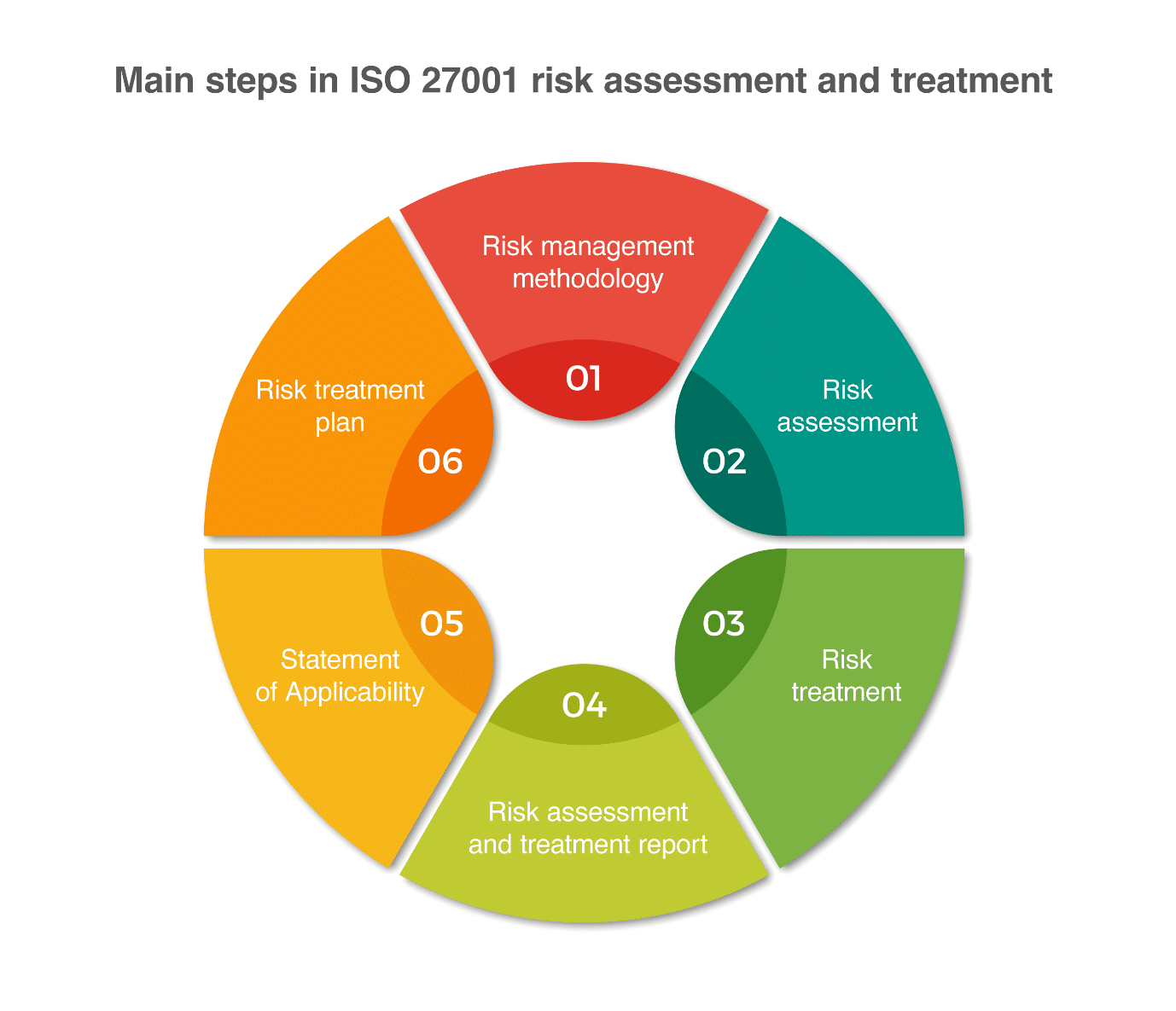
Iso 27001 Risk Assessment Risk Treatment The Complete Guide

Data Quality Assessment Report Template 3 Professional Templates Report Template Data Quality Assessment

Risk Assessment Vs Vulnerability Assessment How To Use Both Bmc Software Blogs

Everything You Need To Know About Security Assessments To Safeguard Your Data
0 comments
Post a Comment